File Integrity Monitoring Market Analysis
The File Integrity Monitoring Market size is estimated at USD 1.20 billion in 2025, and is expected to reach USD 2.65 billion by 2030, at a CAGR of 17.28% during the forecast period (2025-2030).
The file integrity monitoring market is a service that enables organizations to test and check operating system (OS), database, and application software files to determine whether or not they have been tampered with or corrupted documents, photos, videos, and files in a secure manner. Organizations adopt these technologies to help employees avoid using consumer-based file-sharing applications and software to store, access, and manage to ensure data security.
- For instance, enterprises' workstation dominantly uses Windows, Mac OS, and Linux OS. In contrast, their employees utilize mobile devices like tablets and smartphones, with Android and iOS as the dominant operating systems. Due to the widespread adoption of cloud services and an increasing number of active directory users, admins find it difficult to manage privileges and rights granted to the people inside the organization. This has led to an increased vulnerability, which could be disastrous for the organization.
- File integrity monitoring eases the admin process and has been a critical tool in combating cyber threats organizations have recently faced. File integrity monitoring solution monitors the activity of the shared files and is also responsible for timely alerting the admin to minimize the threats.
- The key issue that the file integrity monitoring market resolves is privilege abuses. Privilege abuse is when the policies of the user within the network are not updated, due to which the user's credentials are used to access the files and then make changes to them.
- The landscape of file monitoring and integrity management solution has been changing rapidly. Earlier, the systems admin used to manually grant access and check for vulnerabilities. Still, as the number of events increased, it became impossible for the admins to identify the treats. This gave rise to Netwrix, Lepide, and Dell solutions, which offered standalone solutions for the market. However, these solutions limited the number of users and managed many events.
- The antivirus providers, like Kaspersky and McAfee, realized the importance of this additional layer of security and integrated the solution into their antivirus solutions. However, companies like IBM and SolarWinds have solutions that meet large enterprises' requirements and have advanced methodologies to identify false positives to declutter the notifications sent to the admins.
- During the outbreak of COVID-19, cyber threats were on the rise in numerous countries. For instance, the Australian Cyber Security Centre (ACSC) announced protecting itself from cyberattacks amid the pandemic. Various countries further enhanced their efforts to increase file integrity monitoring systems.
- Cybersecurity became a top priority during the global COVID-19 pandemic. There was an increasing dependence on digital technologies to keep the file integrity monitoring process running. Moreover, according to the US Bureau of Labor Statistics (BLS), from 2022 to 2032, information security analyst employment is expected to grow by 32%, substantially faster than the average for all occupations.
File Integrity Monitoring Market Trends
BFSI Industry is Expected to Witness The Highest Growth
- The BFSI sector is one of the critical infrastructure segments that suffer several data breaches and cyberattacks, owing to the large customer base that the industry serves and the financial information that is at stake. Financial service institutions have been identified to be four times more susceptible to cyberattacks when compared to other industries, which is expected to drive the demand for such solutions.
- Moreover, active directory-based hacking on banking institutions has become the most prevalent recently, according to security provider Bit defender. Also, the need for file integrity monitoring is further emphasized by different warnings sent out by security agencies.
- The security agencies have identified ransomware, like lockerGoga ransomware, and hacking groups, like APT15 - aka K3chang, Mirage, Vixen Panda, GREF, and Playful Dragon, have been most prevalent in attacking the active directory of the BFSI institutions.
- Furthermore, Data breaches lead to an exponential rise in costs and the loss of valuable customer information. For instance, in June 2023, EpiSource LLC notified the Attorney General of California of the data breach after identifying that unauthorized access to sensitive customer data had occurred due to suspicious activity in the company's Amazon Web Services environment. Additionally, in May 2023, the Federal Trade Commission announced that Amazon would pay two distinct fines for privacy violations: USD 25 million for allegedly failing to delete children's data and USD 5.8 million for limiting access to Ring security videos for employees and contractors.
- To secure their IT processes and systems, secure critical customer data, and comply with government regulations, private and public banking institutes focus on implementing the latest technology to prevent cyber attacks. Additionally, with greater customer expectations, increasing technological capabilities, and regulatory requirements, banking institutions are pushed to adopt a proactive approach to security.

Asia-Pacific to Witness Fastest Growth
- Asia-Pacific is estimated to present lucrative opportunities for the market shortly. Factors such as the increased need for security in growing industries, the need to protect high-value targets in organizations, and regulatory compliance are driving the adoption of file integrity monitoring solutions in the region.
- Small and medium-sized businesses are transforming into a hybrid cloud environment in Asia-Pacific from the legacy on-premise environment. Numerous factors have triggered this, as the hybrid cloud environment provides scalability and security concerns.
- Asia-Pacific countries are being used as launchpads for cyber attacks, either as vulnerable hotbeds of unsecured infrastructures where numerous computers can be infected easily for large-scale attacks or as centers for a single point of attack to gain access to the hubs' global connections. So the demand for file integrity monitoring systems is rising in this region.
- China's controversial Cyber Security Law (CSL) is aimed at protecting China's networks and private user information with a new law. It includes power and utility providers, transportation services, and financial institutions, including any foreign company that is a key supplier to a 'critical' sector or holds significant amounts of information on Chinese citizens, increasing the market demand in this country.

File Integrity Monitoring Industry Overview
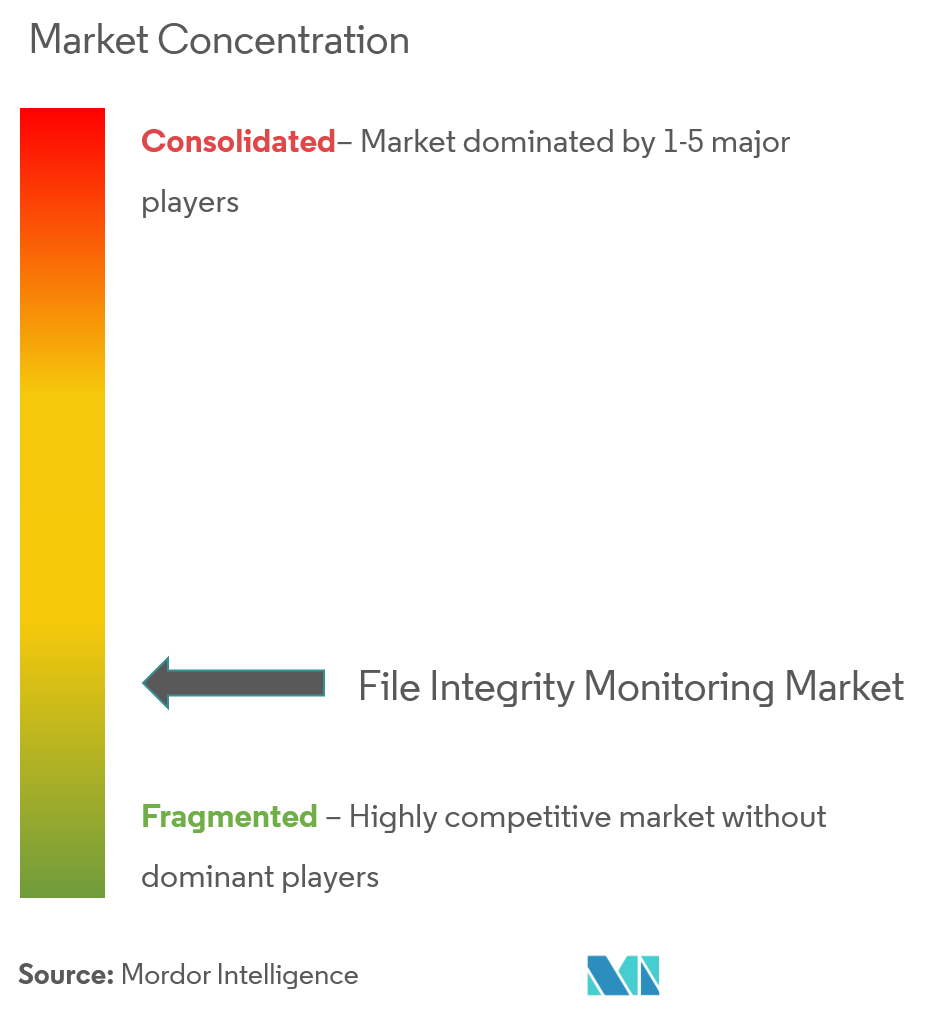
The file integrity monitoring market is fragmented as the vast majority of the global players functioning in the market are taking steps to raise their market footprint by concentrating on product diversification and development. Some of the key players in the market are AT&T, McAfee LLC, Qualys Inc., AlienVault Inc., and Cimcor Inc., among others.
In August 2023, LogRhythm, a global IT security company, and Cimcor, a United States-based security, integrity, and compliance software solutions provider, announced a partnership to develop innovative security and integrity software solutions. Combining Cimcor's file integrity monitoring (FIM) solution, CimTrak, with LogRhythm's comprehensive security information and event management (SIEM) platform, the two companies work together to help organizations all over the world increase visibility and protect against modern cyberattacks.
In February 2023, Qualys, a provider of IT security and compliance platforms, released its GovCloud platform, which it states meets the stringent cybersecurity assurance requirements of FedRAMP at the high impact level. Federal agencies can use Qualys' GovCloud platform to develop and implement cybersecurity programs. One of GovCloud's features includes File Integrity Monitoring, which notifies end users about unauthorized changes to software, firmware, and information in compliance with NIST SI-7 requirements.
File Integrity Monitoring Market Leaders
-
McAfee, LLC
-
Cimcor, Inc.
-
AlienVault, Inc.
-
Qualys, Inc.
-
AT&T
- *Disclaimer: Major Players sorted in no particular order
File Integrity Monitoring Market News
- November 2023 - FileCloud, a secure enterprise file-sharing and content collaboration provider, announced a partnership with Votiro, a player in disarming and delivering safe content, to give clients modern tools to strengthen their security posture. With this partnership, FileCloud is committed to helping businesses avoid possible hazards posed by incoming infected files and collaborating with innovative cybersecurity partners.
- May 2023 - The cloud-native security company Aqua Security has announced the addition of pipeline integrity scanning to guard against supply chain attacks on software and ensure the integrity of the CI/CD pipeline. Teams are able to comprehend the operation of their build pipeline as well as the normal behavior of the file system, the network, and processes in recognized appropriate contexts. Additionally, the solution finds any deviations from the baseline. The scanner can identify any deviation from the baseline and notify teams of anything strange or anomalous, such as unexpected file modification, communication with a suspicious URL, or use of a dropped malicious executable to ensure the integrity of the build process.
File Integrity Monitoring Industry Segmentation
The file integrity monitoring market is a service that enables organizations to test and check operating system (OS), database, and application software files to determine whether or not they have been tampered with or corrupted documents, photos, videos, and files in a secure manner. Large enterprises that utilize file monitoring and integrity solution use it to add flexibility to their access policies that govern the organization's accessibility. The capabilities of the file monitoring and integrity management solution include security features, like authentication and tracking, to protect enterprise data.
The file integrity monitoring market is segmented by organization size (small and medium enterprises, large enterprises), deployment type (on-premises, cloud), installation mode (agent-based, cloud), end-user industry (retail, BFSI, hospitality, healthcare, government, entertainment), and geography (North America, Europe, Asia-Pacific Latin America, Middle East & Africa). The market sizes and forecasts are provided in terms of value (USD) for all the above segments.
| By Organization Size | Small and Medium Enterprises |
| Large Enterprises | |
| By Deployment Type | On-Premise |
| Cloud | |
| By Installation Mode | Agent-Based |
| Cloud | |
| By End-user Industry | Retail |
| BFSI | |
| Hospitality | |
| Healthcare | |
| Government | |
| Entertainment | |
| Other End-user Industries | |
| Geography | North America |
| Europe | |
| Asia-Pacific | |
| Latin America | |
| Middle East & Africa |
File Integrity Monitoring Market Research FAQs
How big is the File Integrity Monitoring Market?
The File Integrity Monitoring Market size is expected to reach USD 1.20 billion in 2025 and grow at a CAGR of 17.28% to reach USD 2.65 billion by 2030.
What is the current File Integrity Monitoring Market size?
In 2025, the File Integrity Monitoring Market size is expected to reach USD 1.20 billion.
Who are the key players in File Integrity Monitoring Market?
McAfee, LLC, Cimcor, Inc., AlienVault, Inc., Qualys, Inc. and AT&T are the major companies operating in the File Integrity Monitoring Market.
Which is the fastest growing region in File Integrity Monitoring Market?
Asia-Pacific is estimated to grow at the highest CAGR over the forecast period (2025-2030).
Which region has the biggest share in File Integrity Monitoring Market?
In 2025, the North America accounts for the largest market share in File Integrity Monitoring Market.
What years does this File Integrity Monitoring Market cover, and what was the market size in 2024?
In 2024, the File Integrity Monitoring Market size was estimated at USD 0.99 billion. The report covers the File Integrity Monitoring Market historical market size for years: 2019, 2020, 2021, 2022, 2023 and 2024. The report also forecasts the File Integrity Monitoring Market size for years: 2025, 2026, 2027, 2028, 2029 and 2030.
Our Best Selling Reports
File Integrity Monitoring Industry Report
Statistics for the 2025 File Integrity Monitoring market share, size and revenue growth rate, created by Mordor Intelligence™ Industry Reports. File Integrity Monitoring analysis includes a market forecast outlook for 2025 to 2030 and historical overview. Get a sample of this industry analysis as a free report PDF download.