Retail Cloud Security Market Size and Share

Retail Cloud Security Market Analysis by Mordor Intelligence
The Retail Cloud Security Market size is estimated at USD 5.83 billion in 2025, and is expected to reach USD 10.95 billion by 2030, at a CAGR of 13.44% during the forecast period (2025-2030).
Due to technological development and the vast amount of information available in digital form, data breaches are frequent. According to IBM's Cost of a Data Breach Study 2022, the average data breach cost was 4.35 million USD in 2022. Businesses implement all-encompassing preventative actions to close any potential system vulnerabilities, from end users to IT systems, leading to the adoption and growth of the cloud security market.
- Forecasting how the retail business will perform over the next few years is challenging due to the ongoing change in consumer purchasing behavior. To withstand competition, retailers must consistently innovate, guarantee precision, and maintain synchronization. Many retailers adopted cloud solutions to store confidential information securely and inventory online within the cloud. This technological shift demanded a secure network solution, which Cloud Security providers are guarding.
- The COVID-19 pandemic pushed more consumers online. Retailers employed analytics to understand better consumer demands and AI-powered processes to give what they want. With the digital transformation in the retail industry, cloud storage has become a need, increasing the demand for cloud security services.
- According to Trend Micro, 91 percent of all cyberattacks start with an email "spear-phishing" attempt directed at a particular employee within an organization. The retail sector employs many unskilled employees so human factors may contribute to many data security issues. Employees must be educated about the various data security dangers and how to handle them; otherwise, it will be difficult for the cloud security industry to protect the data from untimely attacks.
Global Retail Cloud Security Market Trends and Insights
Intrusion Detection and Prevention to Register a Significant Growth
- When malicious activity is detected, an intrusion detection system (IDS) monitors network traffic and immediately provides alarms. The intrusion detector learning task is to build on a predictive model that can differentiate between bad connections, such as intrusions and attacks, and good connections. The system administrator can then investigate the alert and act to prevent damage.
- Different types of Intrusion Detection Systems (IDS) exist, depending on the software requirement. For instance, Cisco developed an Intrusion Prevention System (IPS), which provides network intrusion detection and prevention mode functionalities. Users can enable Snort in IPS or IDS mode based on their needs.
- According to Verizon's 2023 Data Breach Investigations Report,83% of breaches involved external factors with finanfial motives, retail, financial and healthcare sector has been seen at forefront of such attacked.These attacks were primarily made to steal customer data for profit.
- Many retailers invest in contactless transaction technologies that use IoT to process payments. These innovations contribute to human health protection and increase cyber threats. Attackers use sophisticated bot networks to collect data like credit card numbers or login credentials. Government agencies have started demanding MFA (multi-factor authentication) for systems that handle sensitive data in response to the rising tide of cyberattacks.

Asia-Pacific to Witness the Highest Growth
- The retail sector suffers an average of 4,000 data security threats every year. In 2022, the Asia-Pacific area experienced the most cyberattacks for the second consecutive year, with 31% of all incidents remedied globally.
- According to the X-Force Threat Intelligence Index, spear phishing via attachment was discovered to be the leading infection vector at 40%. Ransomware was used in 13% of incidents, while backdoor deployment, which grants attackers remote access to systems, accounted for 31% of attacks.
- In March 2023, Keeper Security collaborated with Daiwabo Information System Co., Ltd. (DIS) to distribute security solutions across 19,000 sales partners and 90 bases to help protect Japanese businesses and customers from cyberattacks and data breaches. The Keeper platform is scalable to meet the demands of any size organization, deploys within minutes, and requires very little ongoing management. Furthermore, the solution can seamlessly interact with any security stack and data environment, including single-cloud, multi-cloud, and hybrid.

Competitive Landscape
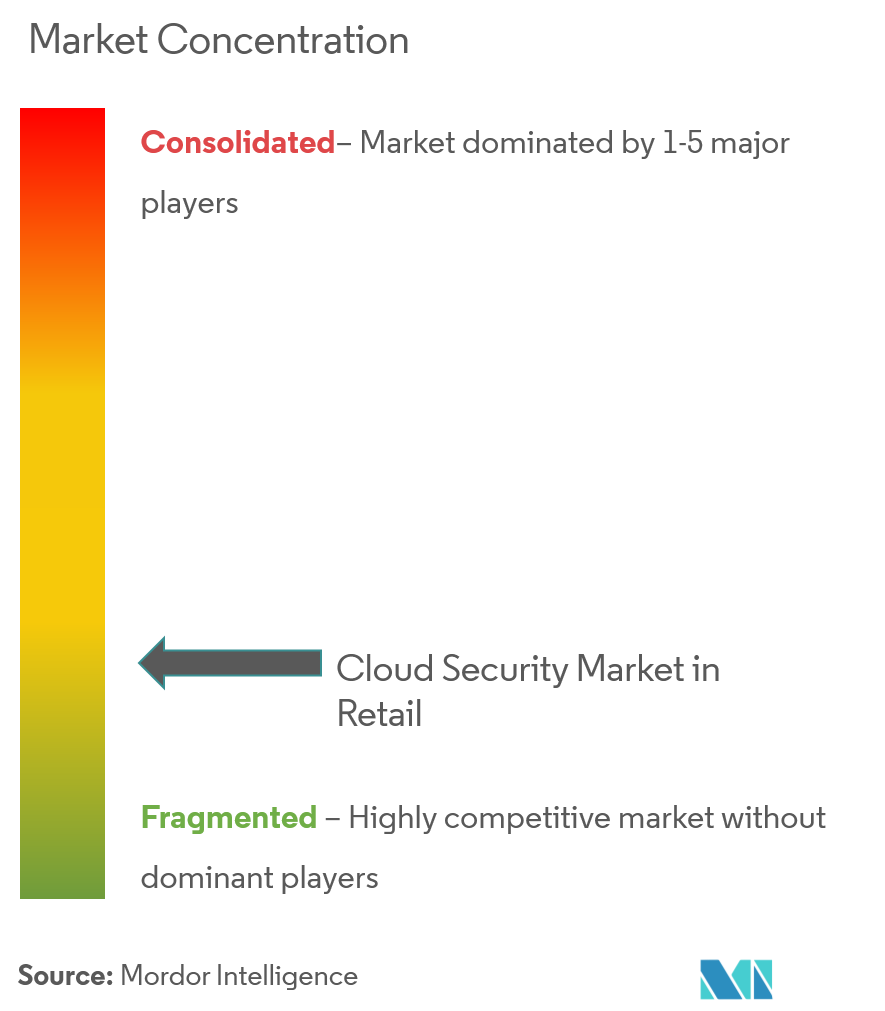
There is intense competition with several providers of Cloud Security, because of which market concentration will be low. Almost every industry is transitioning from on-premises to digital platforms for corporate activity. With rapid digitalization, cyber-attacks and data breaches have increased. Thus, businesses are compelled to opt for cloud security solutions. Some significant cloud security providers in this sector include IBM Corporation, Trend Micro Inc., McAfee, Broadcom Inc., and Cisco Systems Inc. With new product solutions and services, mergers and acquisitions, and strategic collaborations, these Cloud security player are expanding their reach in different industries and geographies.
In February 2023, Cisco acquired Valtix to enhance its security cloud portfolio. The cloud solution designed by Valtix can achieve 100% security coverage through continuous discovery and takes 30 seconds to adapt to new apps and modifications to existing apps dynamically. The integration will fasten Cisco's progress towards providing an easy-to-use environment for safeguarding workloads across multi-cloud settings.
In October 2022, Beyon Cyber and Trend Micro partnered to boost Bahrain's cybersecurity framework. According to the agreement, the companies will detect cyber threats in real time, take preemptive measures to contain them and reduce risk and harm, giving the nation's organizations complete insight to safeguard all digital environments with full visibility and control.
In May 2022, Thailand-based retail company TD Tawandang collaborated with Google Cloud to provide a retail-as-a-service platform to its customers. Adopting Google Cloud's secure and scalable infrastructure, advanced analytics, artificial intelligence (AI), and machine learning (ML) technologies will help convenience store chains with more streamlined backend services.
Retail Cloud Security Industry Leaders
-
Trend Micro Inc.
-
Imperva Inc.
-
Broadcom Inc.
-
IBM Corporation
-
Cisco Systems Inc.
- *Disclaimer: Major Players sorted in no particular order
Recent Industry Developments
- March 2023: IBM revised its Storage Defender solution by adding Cohesity data protection. Cohesive Data Protect’s integration into IBM Storage Defender will boost business resilience for organizations’ hybrid cloud systems by minimizing data fragmentation and maximizing availability. Cohesity DataProtect positions clients to copy and store data on numerous servers, on-site or off-site, or in various clouds. In the event of a disaster or cyber security breach, this helps to ensure that a current and exact copy of the data is available.
- January 2023: HDFC Bank adopted Microsoft’s Azure to consolidate and modernize its enterprise data landscape, scaling its information management capabilities across enterprise reporting and advanced analytics through artificial intelligence. Using the Microsoft Cloud Platform and technology built on AI/ML, uniform architecture, and security, The solution will provide consumers with stringent security and regulatory requirements.
- December 2022: Tata Motor signed a deal with Oracle for its cloud solutions that would provide enhanced business insights, improved security, increased flexibility, and reduced costs. The automotive player was to transform its Dealer Management System (DMS), which contains data of 60,000 customers, to Oracle Cloud Infrastructure. Oracle was expected to help the automotive leader monitor sales performance and share insights to improve collaboration across its dealer network.
Global Retail Cloud Security Market Report Scope
The security practices and technologies that protect data and systems in a business's Internet of Things environment shall be called Cloud Security for Retail. It is necessary to ensure that confidential customer data, e.g., payment information and identity documents, are kept safe when dealt with by retail enterprises to protect them from potential unauthorized access or misuse.
The cloud security market in retail can be segmented by solution (identity and access management, data loss prevention, IDS/IPS, security information and event management, and encryption), security (application security, database security, endpoint security, network security, and web and email security), deployment mode (private, hybrid, and public), and geography (North America (US and Canada), Europe (Germany, UK, France, Rest of Europe), Asia-Pacific (India, China, Japan, and Rest of Asia-Pacific), Latin America, Middle East & Africa). The market sizes and forecasts are provided in terms of value (USD).
| Identity and Access Management |
| Data Loss Prevention |
| Intrusion Detection and Prevention |
| Security Information and Event Management |
| Encryption |
| Application Security |
| Database Security |
| Endpoint Security |
| Network Security |
| Web and Email Security |
| Private |
| Hybrid |
| Public |
| North America | US |
| Canada | |
| Europe | Germany |
| UK | |
| France | |
| Rest of Europe | |
| Asia-Pacific | India |
| China | |
| Japan | |
| Rest of Asia-Pacific | |
| Latin America | |
| Middle East and Africa |
| By Solution | Identity and Access Management | |
| Data Loss Prevention | ||
| Intrusion Detection and Prevention | ||
| Security Information and Event Management | ||
| Encryption | ||
| By Security | Application Security | |
| Database Security | ||
| Endpoint Security | ||
| Network Security | ||
| Web and Email Security | ||
| By Deployment Mode | Private | |
| Hybrid | ||
| Public | ||
| By Geography | North America | US |
| Canada | ||
| Europe | Germany | |
| UK | ||
| France | ||
| Rest of Europe | ||
| Asia-Pacific | India | |
| China | ||
| Japan | ||
| Rest of Asia-Pacific | ||
| Latin America | ||
| Middle East and Africa | ||
Key Questions Answered in the Report
How big is the Retail Cloud Security Market?
The Retail Cloud Security Market size is expected to reach USD 5.83 billion in 2025 and grow at a CAGR of 13.44% to reach USD 10.95 billion by 2030.
What is the current Retail Cloud Security Market size?
In 2025, the Retail Cloud Security Market size is expected to reach USD 5.83 billion.
Who are the key players in Retail Cloud Security Market?
Trend Micro Inc., Imperva Inc., Broadcom Inc., IBM Corporation and Cisco Systems Inc. are the major companies operating in the Retail Cloud Security Market.
Which is the fastest growing region in Retail Cloud Security Market?
Asia Pacific is estimated to grow at the highest CAGR over the forecast period (2025-2030).
Which region has the biggest share in Retail Cloud Security Market?
In 2025, the North America accounts for the largest market share in Retail Cloud Security Market.
What years does this Retail Cloud Security Market cover, and what was the market size in 2024?
In 2024, the Retail Cloud Security Market size was estimated at USD 5.05 billion. The report covers the Retail Cloud Security Market historical market size for years: 2019, 2020, 2021, 2022, 2023 and 2024. The report also forecasts the Retail Cloud Security Market size for years: 2025, 2026, 2027, 2028, 2029 and 2030.
Page last updated on:
Retail Cloud Security Market Report
Statistics for the 2025 Retail Cloud Security market share, size and revenue growth rate, created by Mordor Intelligence™ Industry Reports. Retail Cloud Security analysis includes a market forecast outlook for 2025 to 2030 and historical overview. Get a sample of this industry analysis as a free report PDF download.